windows firewall log event viewer
Under Logging click Customize. There is no need to restart the computer after you enable the rules.

Security Windows Firewall Logging Notifying On Outgoing Request Attempts Super User
Ill definitely add that to my arsenal.

. The default path for the log is windirsystem32logfilesfirewallpfirewalllog. To access thee advanced firewall click on the Advanced settings link in the left hand side. Make sure its set to Running and Automatic.
You should be able to see this in Event Viewer. This error can be fixed with special software that repairs the registry and tunes up system settings to restore stability. You can use the Windows event logs to monitor Windows Firewall and IPsec activity and to troubleshoot issues that may arise.
Inside the Properties tab select the Customize button under Logging. Enable COM Network Access DCOM-In. Event Viewer and Firewall Logs is commonly caused by incorrectly configured system settings or irregular entries in the Windows registry.
There you can create a custom view and filter the log to only outbound connection attempts. The default path for the log is windirsystem32logfilesfirewallpfirewalllog. From right side panel select Filter log Keywords Select Audit failure.
Wireshark Go Deep. Applications and Services LogsMicrosoftWindowsWindows Firewall With Advanced Security. In the Windows Control Panel select Security and select Windows Firewall with Advanced Security.
Select Inbound Rules and in the. Or get a better GUI for Windows Firewall like GlassWire not sure about its logs though. On the main Windows Firewall with Advanced Security screen scroll down until you see the Monitoring link.
Interpreting the Windows Firewall log. You can connect to the target computer immediately. I added an exception to the firewall and a modification to the firewall.
To do this follow these steps. Click the tab that corresponds to the network location type. This is the default setting unless firewall rules have been set up for specific applications in Windows Firewall.
If you want to change this. You can track it to look for a potential Pass-the-Hash PtH attack. Windows security event log ID 4672.
The Windows Firewall security log contains two sections. Press OK to close the Logging Settings menu and again to close the Windows Defender Firewall Properties. Check the Status and Startup Type.
Information that can be found here are application name destination IP connection direction and more. If you have a standard or baseline for Windows Firewall settings defined monitor this event and check whether the settings reported by the event are still the same as were defined in your standard or baseline. Interpreting the Windows Firewall log.
On 9th April 2020. Under Logging click Customize. At any rate as the description says Windows Firewall prevented an application from accepting incoming connections due to absence of an appropriate Exception in the current profiles policy.
Auditing changes made to firewall configurations allows. Right-click the Start charm and then click Computer Management. Enable all the rules in the Remote Event Log Management group.
This event log contains the following information. Select the Windows Defender Firewall tab and click Properties in the Actions menu. I then went to Event Viewer Application and Services Logs Microsoft Windows Windows Firewall with Advanced Security Firewall.
Press OK to close the Logging Settings menu and again to close the Windows Defender Firewall Properties. For 4950 S. Free Security Log Quick Reference Chart.
Using a Windows Firewall log analyzer such as EventLog Analyzer empowers you to monitor Windows Firewall activity with its comprehensive predefined graphical reports as well as analyze this information to gain useful insights. So it is important for security administrators to audit their Windows Firewall event log data. Rather than focusing on Windows Firewall log focus on network traffic logs instead.
Open event viewer and go to Windows logs Security. In the details pane in the Overview section click Windows Defender Firewall Properties. Press WinR and type servicesmsc in the Run dialog box.
In the navigation tree expand Event Viewer expand Applications and Services expand Microsoft expand Windows and then expand Windows Firewall with Advanced Security. This event informs you whenever an administrator equivalent account logs onto the system. If the SubjectSecurity ID in the Event Viewer doesnt contain LocalSystem NetworkService LocalService its not an admin-equivalent account and requires.
Four event logs you can use for monitoring and. Verify you are able to read the log. Free Security Log Resources by Randy.
Select Yes in the Log Dropped Packets dropdown menu. Setting Up Windows Firewall to Allow Remote Event Log Management. In the Event Viewers left pane expand to Applications and Services Log - Microsoft - Windows - Windows Firewall with Advanced Security.
On Windows 10 the Event Viewer is a handy legacy tool designed to aggregate event logs from apps and system components into an easily digestible structure which you can then analyze to. The event logs for Windows Firewall are found under the following location in Event Viewer. Scroll to Windows Firewall and Event log.
In the details pane in the Overview section click Windows Firewall Properties. The event logs for Windows Firewall are found under the following location in Event Viewer. This event log contains the following information.
For each network location type Domain Private Public perform the following steps. Press Enter to open Services window. First youll need to tweak the logging options in the Advanced Settings Console.
Event Viewer is available as part of Computer Management. I got an easier way to check event log using PowerShell command below. For each network location type Domain Private Public perform the following steps.
If not right-click the service and select. In the Details pane under Logging Settings click the file path next to File Name The log opens in Notepad. A Windows Firewall setting has changed.
To configure Active Directory domain controllers and Exchange servers to allow Juniper Identity Management Service to connect when the host Windows Firewall is enabled. When the Windows Filtering Platform blocks an application from accepting any incoming connections on the network event ID 5031 is logged. This event can be helpful in case you want to monitor all changes in Windows.
Click the tab that corresponds to the network location type. Event Viewer is available as part of Computer Management. Based on the changed I made the event viewer gave me events 2002 2004 an exception 2005 modification of a rule.

4950 S A Windows Firewall Setting Has Changed Windows 10 Windows Security Microsoft Docs
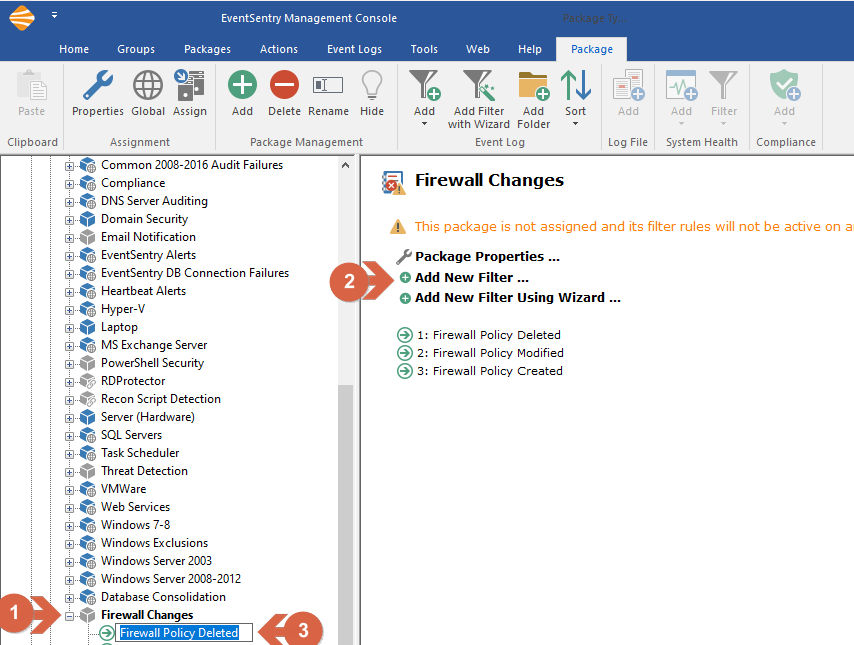
How Can I Be Alerted If Microsoft Windows Firewall Policies Change Eventsentry
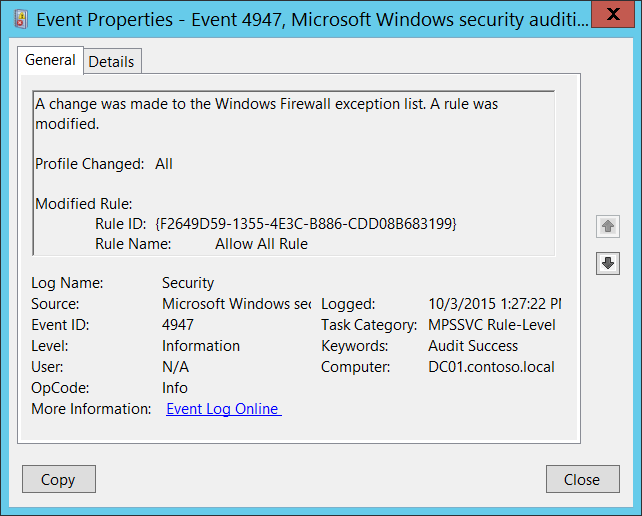
4947 S A Change Has Been Made To Windows Firewall Exception List A Rule Was Modified Windows 10 Windows Security Microsoft Docs

Log Record Event An Overview Sciencedirect Topics

Security Windows Firewall Logging Notifying On Outgoing Request Attempts Super User

How To Setup Windows Firewall Logging And Tracking Techspeeder

4944 S The Following Policy Was Active When The Windows Firewall Started Windows 10 Windows Security Microsoft Docs

Issue Collecting Windows Firewall Events Microsoft Tech Community
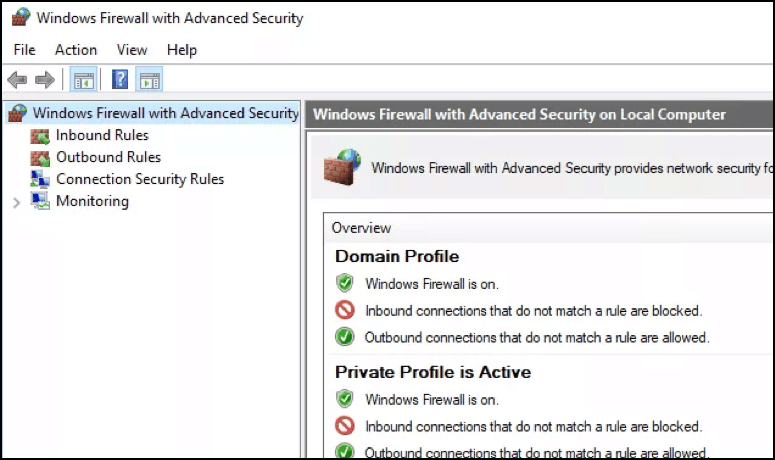
The Significance And Role Of Firewall Logs
0 Response to "windows firewall log event viewer"
Post a Comment